实验课写写之前做过的题叭
Guess-the-Number
下载文件,得到一个jar包,解压得到一个class文件
这个地方要用到一个反编译插件jadclipse,得到guess.class文件的源代码如下(全部)。
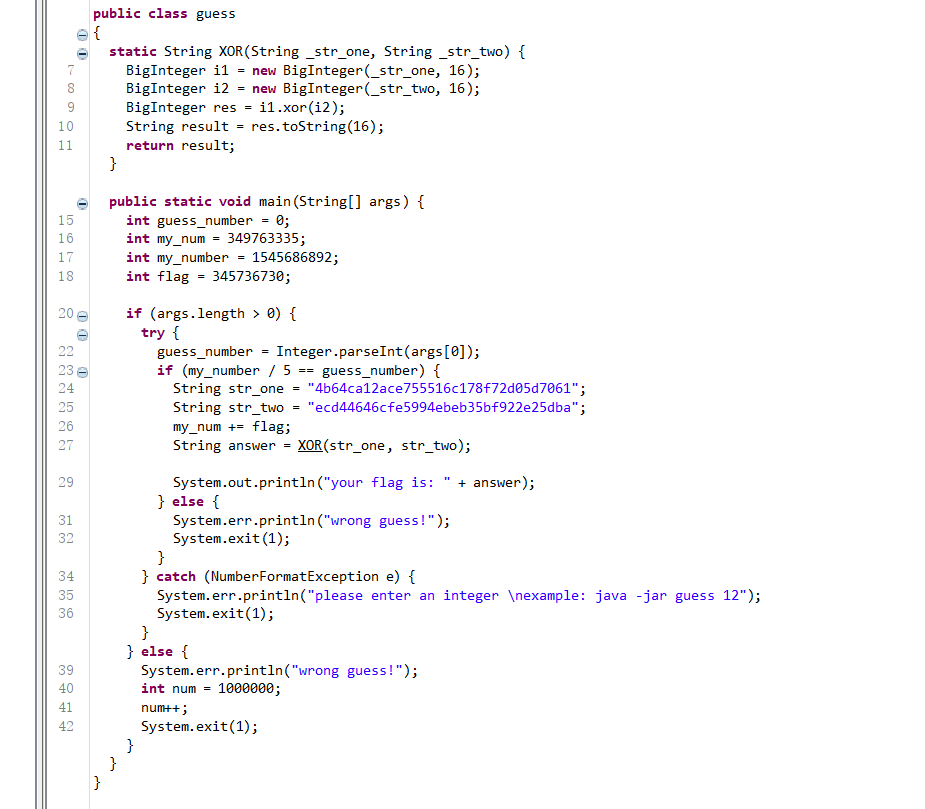
if (my_number / 5 == guess_number) {//可求得guess_number为309137378,
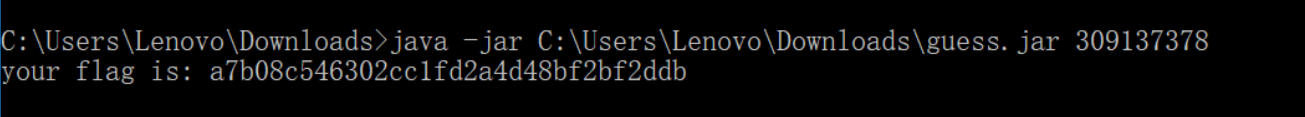
输入命令java -jar guess.jar 309137378
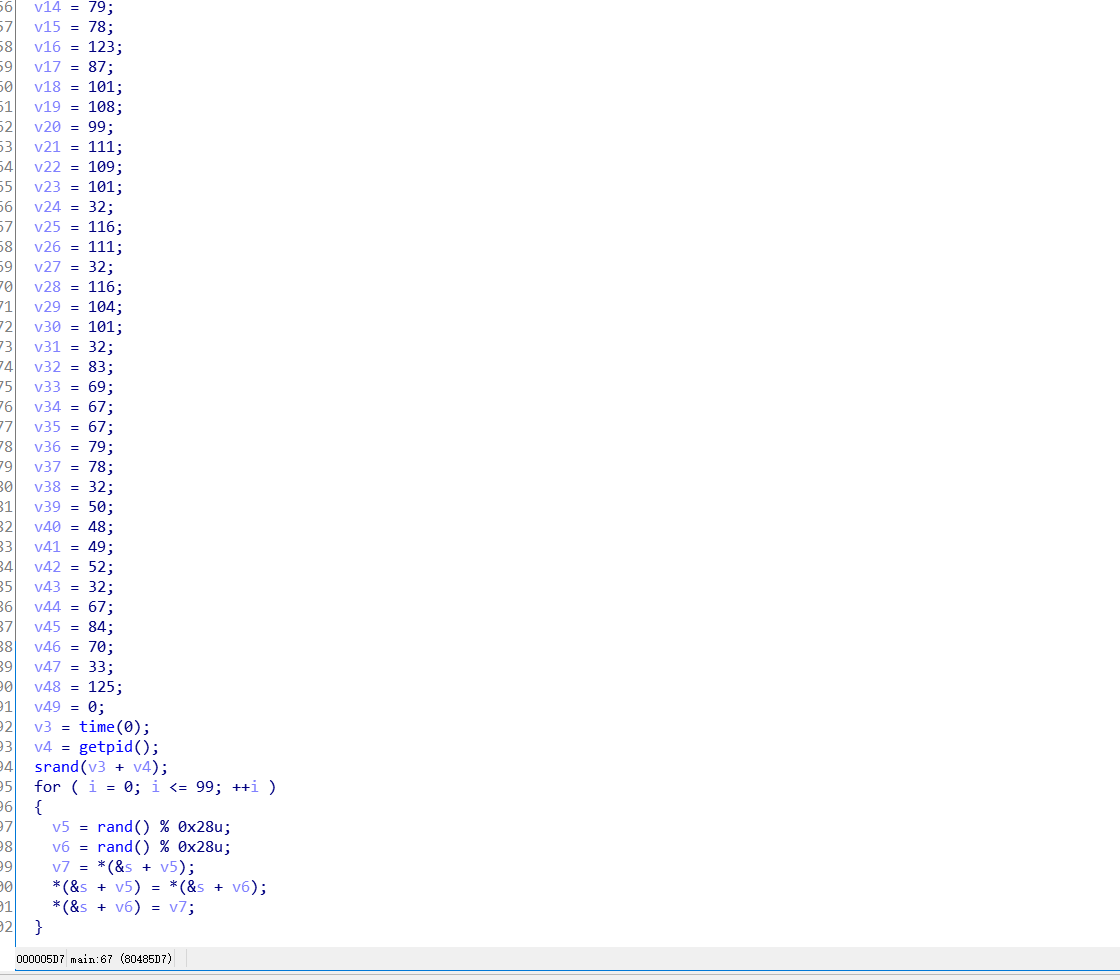
Shuffle
查看是32位文件,拖入ida查看,F5
按R查看字符串得到flag

re-for-50-plz-50
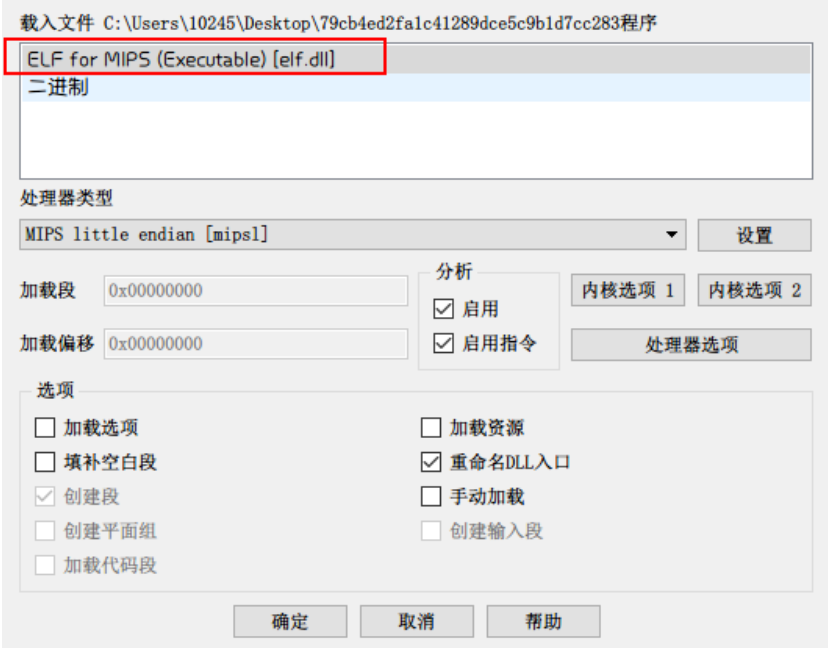
打开ida,发现这是MIPS代码。本来准备安装RetDec,哎…还是恶补MIPS指令知识吧:https://www.cnblogs.com/thoupin/p/4018455.html
分析重点

这实际上就是一个对字符串的异或操作
str1 = 'cbtcqLUBChERV[[Nh@_X^D]X_YPV[CJ' |
dmd-50
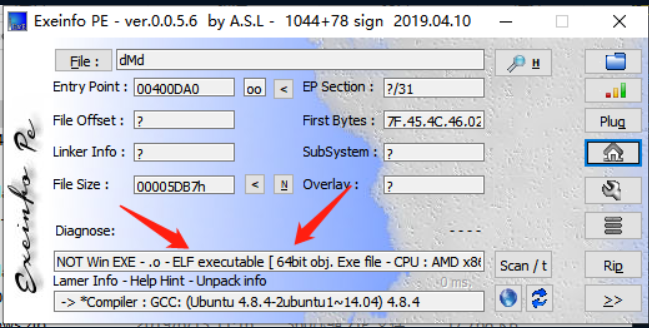
可以看到是ELF64位文件,需要在linux环境运行
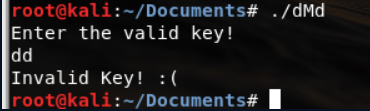
可以看到需要输入正确的key
F5查看伪代码,发现是md5加密。
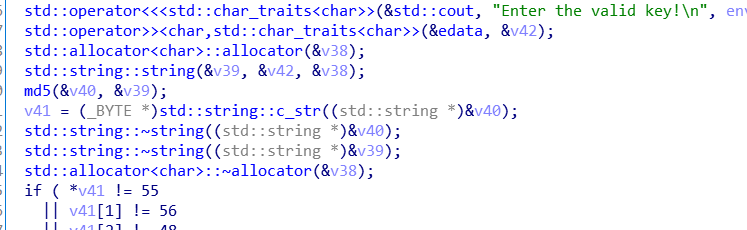
然后我们继续往下看,从if判断条件中,可以得知加密后的密文
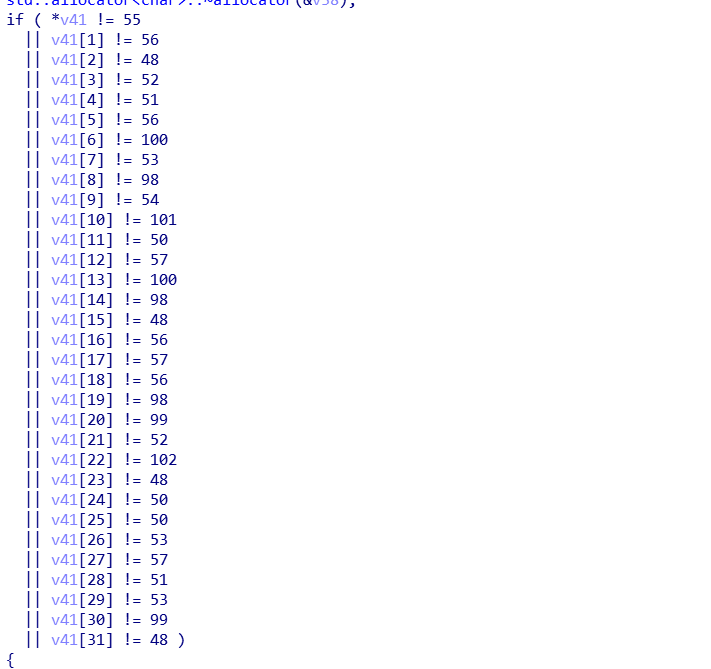
编写脚本
parallel-comparator-200
C文件
|
粗略看一遍,发现 pthread_t 以及pthread_join pthread_create函数看不懂,于是网上查资料,得知
pthread_t
typedef unsigned __int64 uintptr_t |
pthread_create :作用为创建新线程,如果创建成功则返回0,否则返回error number``
int pthread_create(pthread_t *thread, const pthread_attr_t *attr,void *(*start_routine)(void*), void *arg); |
pthread_t *thread是线程的标识符pthread_attr_t *attr用来设置线程属性(如果为NULL,则为默认属性}void *(*start_routine)(void*)是运行函数的起始地址void *arg运行函数的参数
prhread_join : 作用为等待一个线程的结束,如果成功则返回0,否则返回error number``
int pthread_join(pthread_t thread, void **value_ptr); |
pthread_t thread线程标识符void **value_ptr存储被等待线程的返回值
有了以上知识,可以很容易可以知道user_string[20] (输入数组)的每个元素加上first_letter(经调试为固定值108),然后再与 differences[20]的元素异或,最后与just_a_string[20]的元素进行比较,用代码描述就是:
strcmp( ( user_string[i] + first_letter ) ^ differences[i] , just_a_string[i] ) |
脚本:
1 a = [0, 9, -9, -1, 13, -13, -4, -11, -9, -1, -7, 6, -13, 13, 3, 9, -13, -11, 6, -7] |
secret-galaxy-300
运行程序
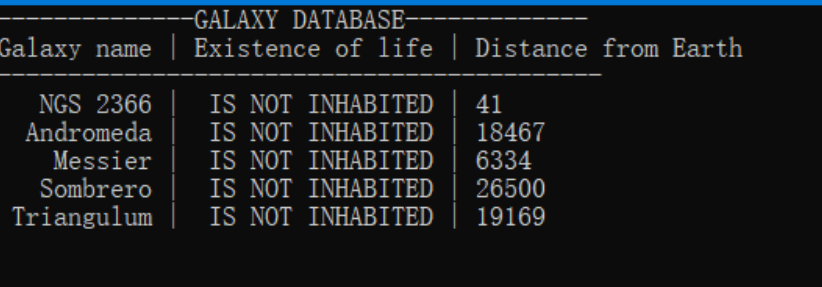
ida查看字符串
动态调试,看运行后内存信息
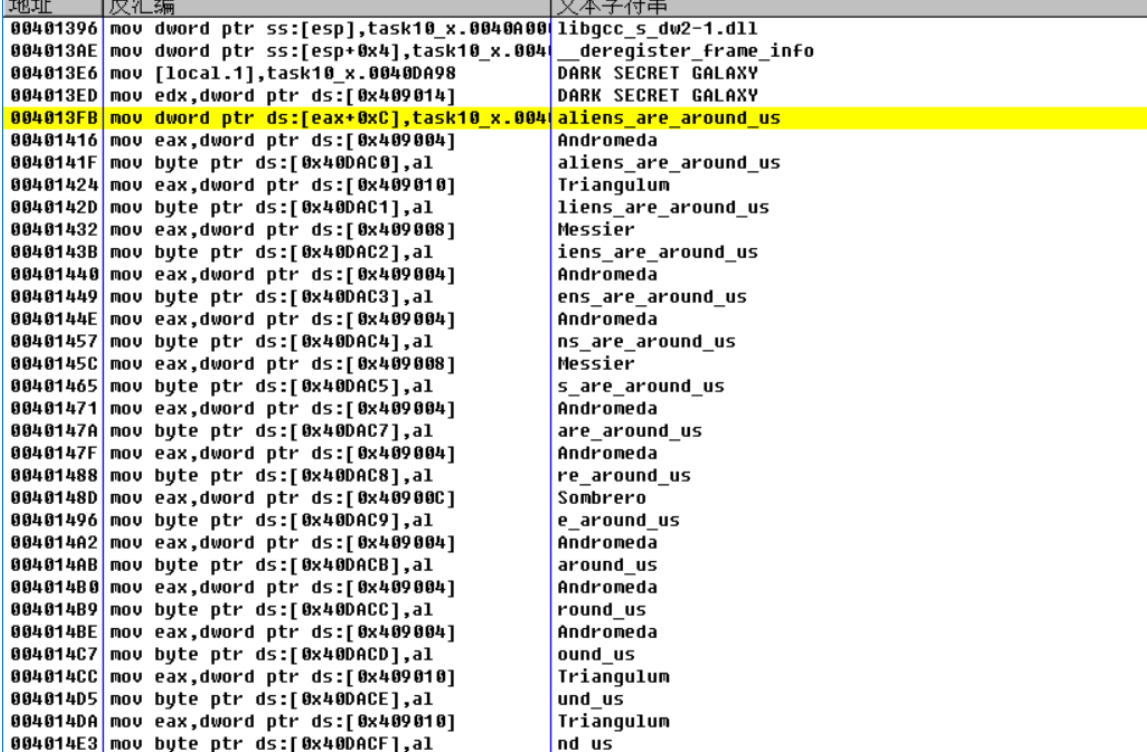
发现了一串字符 aliens_are_around_us提交,成功。
srm-50
exe文件
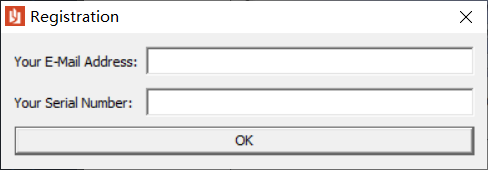
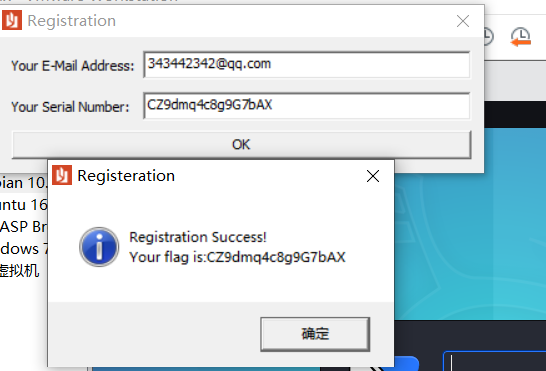
运行程序,可知是 MFC 框架的对话框程序,随便输入数据,显示注册失败。IDA 静态分析 IDA 分析,找到 winmain,是 MFC 的主函数

读程序可知先是验证邮箱的合法性,然后验证 v11,可推测 flag 长度为 16,但是 v11 是 一个长度为 4 的 char 数组 CHAR v11[4],如果输入超过四位就到 v12-v23,刚好 16 个。
编写程序
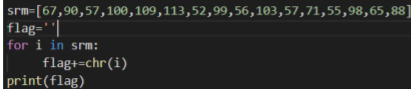
得到flag
simple-check-100
这道题值得记录一下,因为这道题让我第一次接触peda。
1 int __cdecl main(int argc, const char **argv, const char **envp) |
很明显只要绕过第76行代码,我们就能够获取我们需要的flag,而且v8还是已知的
将Linux下的那个文件放入Linux调试。
task9_x86_64_46d01fe312d35ecf69c4ff8ab8ace75d080891dc
命令
gdb |
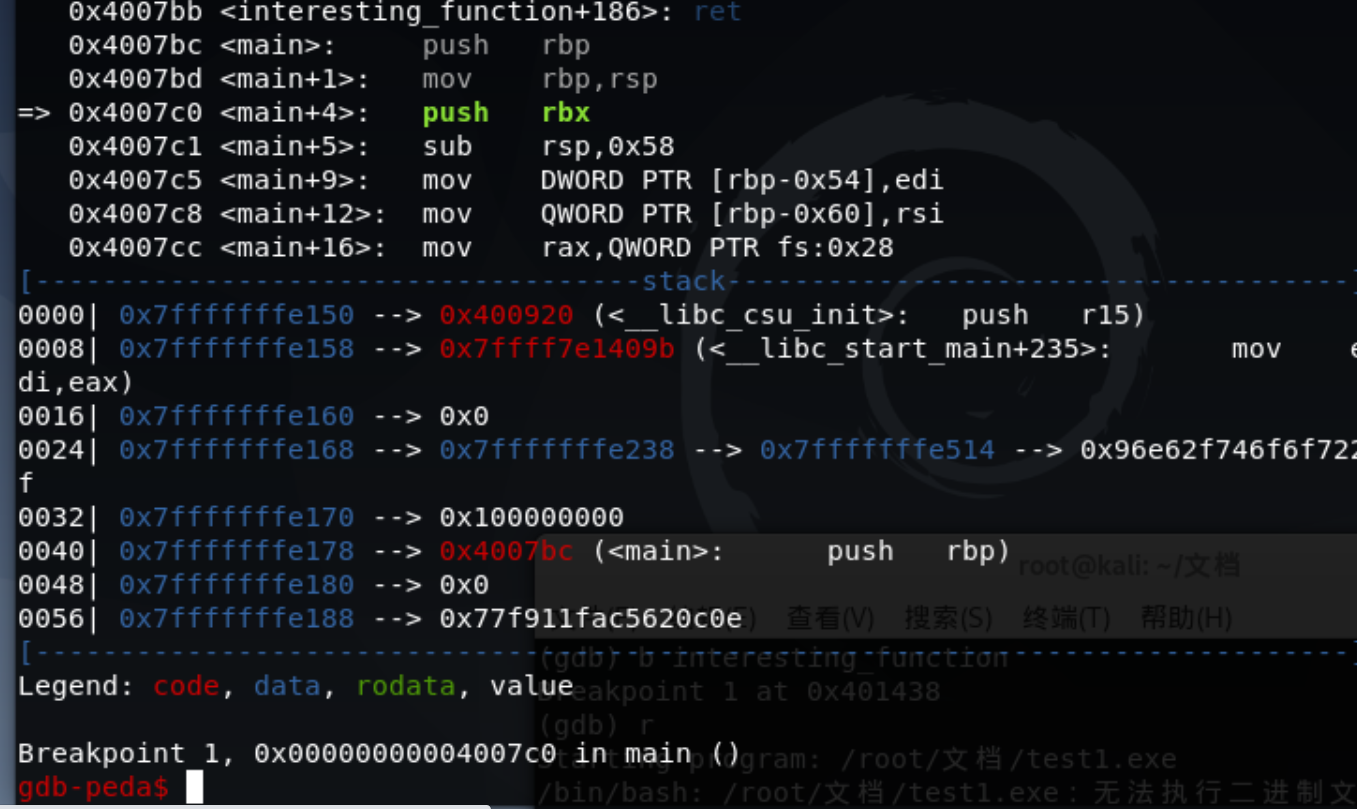
然后一直执行命令next,运行到check_key函数处
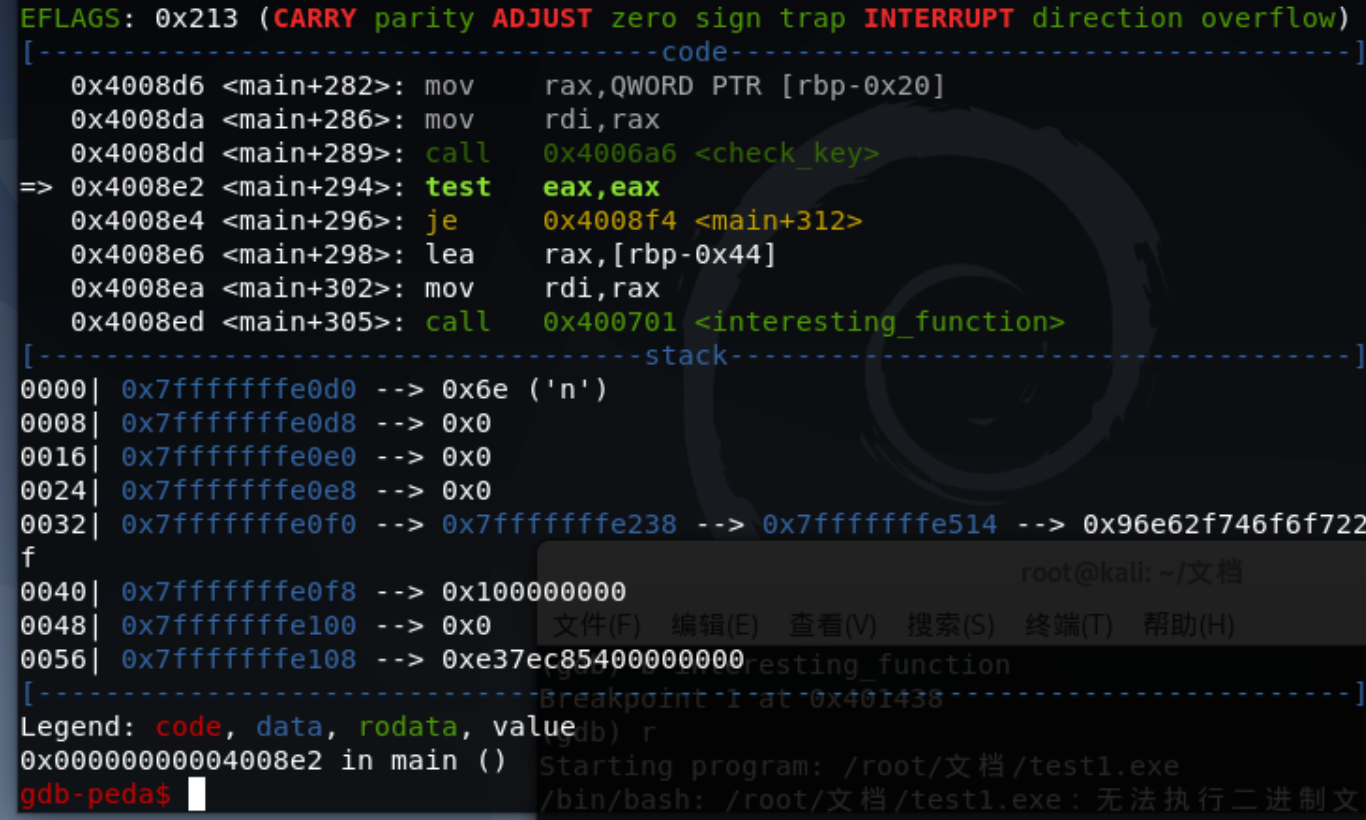
把test eax,eax改为真就行,也就是把eax改为1。
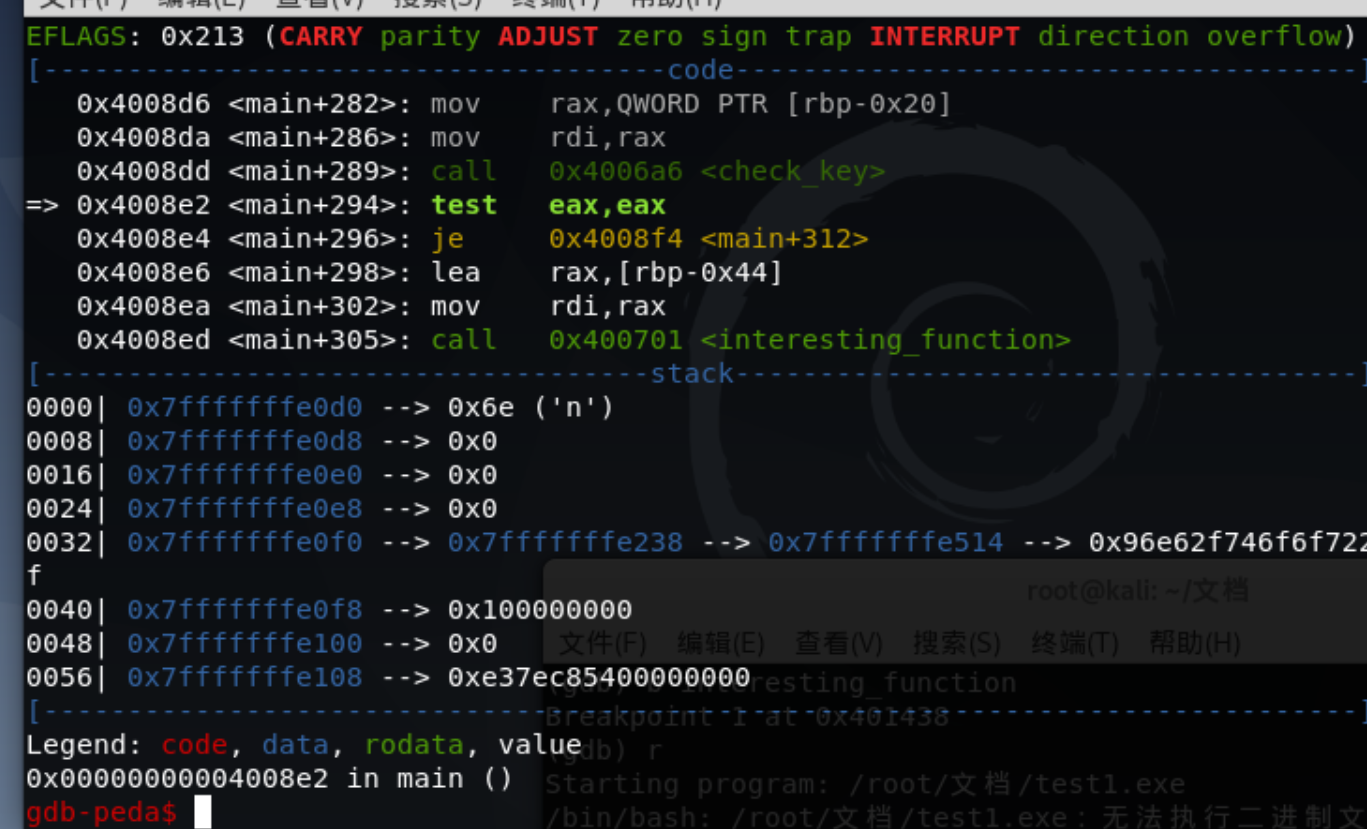
修改eax
set $eax=1 |
Mysterious
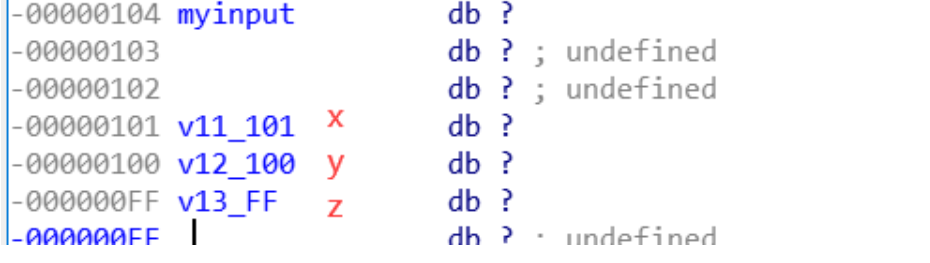
int __stdcall sub_401090(HWND hWnd, int a2, int a3, int a4) |
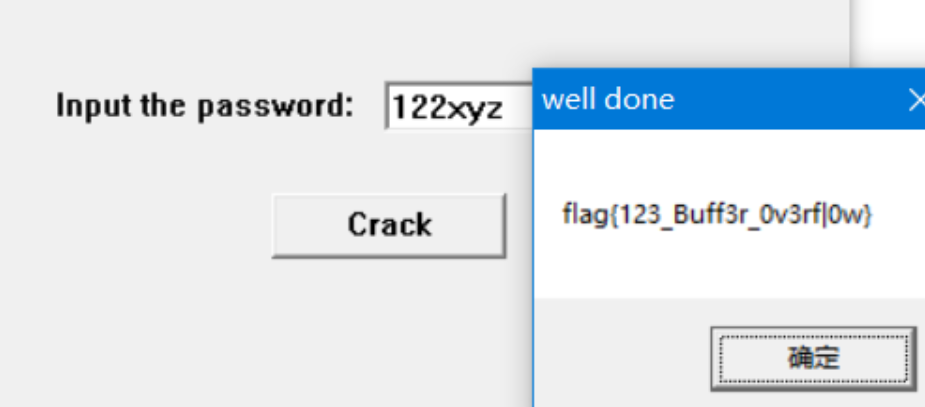
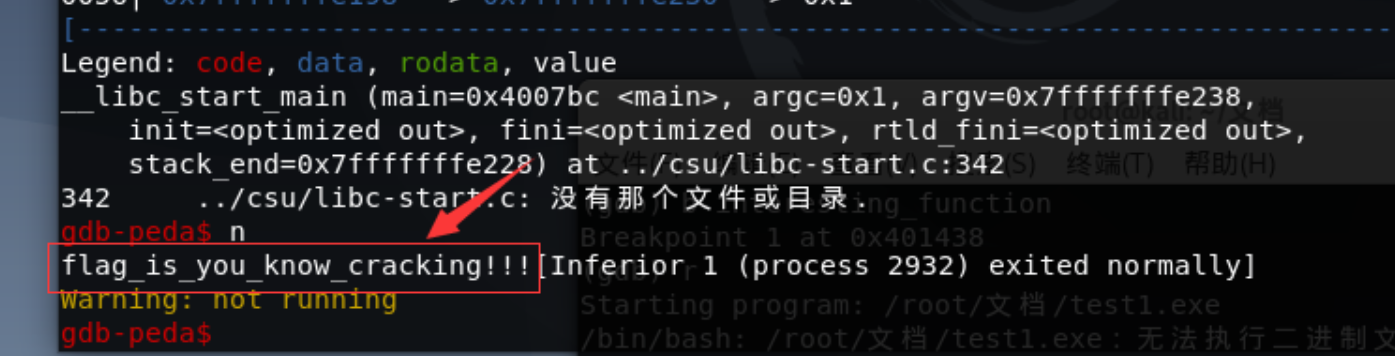
flag{123_Buff3r_0v3rf|0w}
Newbie_calculations
题目名百度翻译成新手计算,那我猜应该是个实现计算器的题目。。。。
IDA打开程序,发现一长串的函数反复调用,而且程序没有输入,只有输出。额,那这样的话程序运行就应该输出flag,但程序中肯定会有垃圾循环操作,就让你跑不出来。
这种题目就要分析函数作用,简化,自己实现算法。
for ( i = 0; i < 32; ++i ) |
这道题目的关键就在于如何识别出上面这些函数的作用
_DWORD *__cdecl mul_401100(_DWORD *a1, int a2) |
1 int *__cdecl add_401000(int *a1, int a2) |
_DWORD *__cdecl sub_401220(_DWORD *a1, int a2) |
WP
def mul_401100(a,b): |
re1-100
这题竟然放在了高手区
1 if ( numRead ) |
主要分析confuseKey(bufParentRead, 42)函数
1 bool __cdecl confuseKey(char *szKey, int iKeyLength) |
exp
1 s1=‘53fc275d81‘ |
answer_to_everything
main.exe 打开

查壳
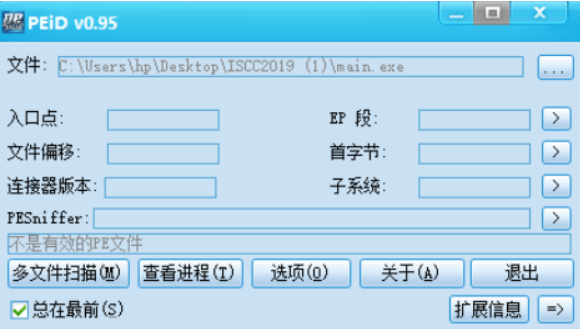
不是有效的PE文件 即不是window 平台运行的软件 猜测是linux
将main.exe拖入ida 32
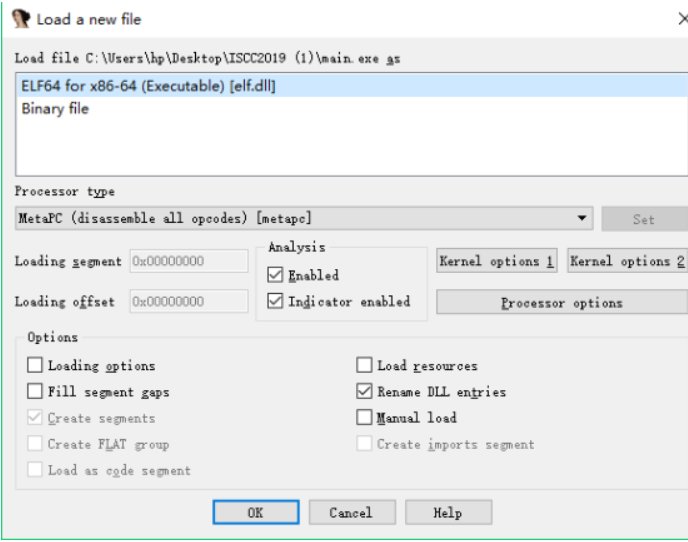
得到信息 ELF64 for x86-64 elf即代表是在linux下运行的软件 64 代表 ida 32 分析不了这个 程序 得用ida 64 分析
所以现在拖入linux里 (ubuntu 64)
打开终端
然后查看 main.exe的权限 ls -a main.exe 然后显示
chmod a+x main.exe//变为可执行 //如果权限不够的话执行改命令 发现 -rwxrwxrwx此时有权限执行main.exe
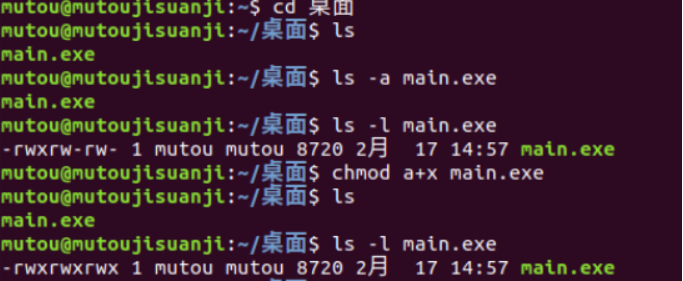
然后输入命令 ./main.exe
显示
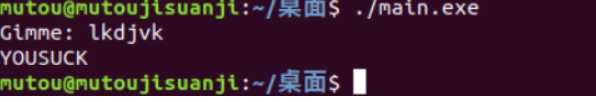
然后随便输入
然后提示 YOUSUCK//你真笨 猜测 这个程序 先输出一句话 Gimme 然后又输入东西 错误的话 输出 YOUFUCK 正确的话 输出我们想要的信息
接下来 将main.exe 拖入ida 64 查找 关键字符串 Gimme//因为很少直接看到了就不用再搜索了

双击 进去与之对应的代码段 可以看到
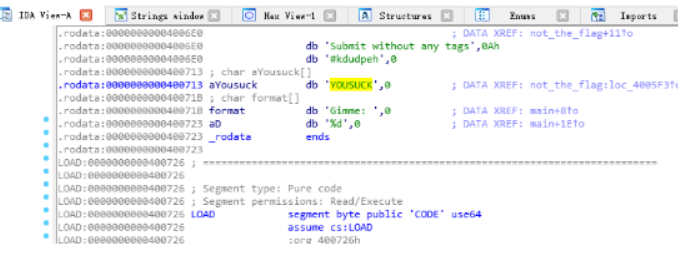
然后敲击键盘上的x键可查看那几个引用它了 敲击 X 键
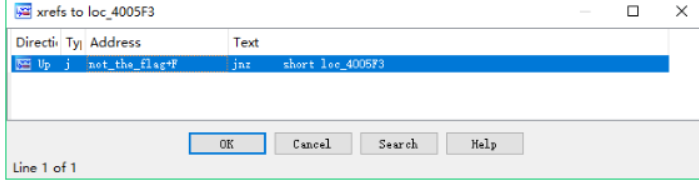
点进去为一个函数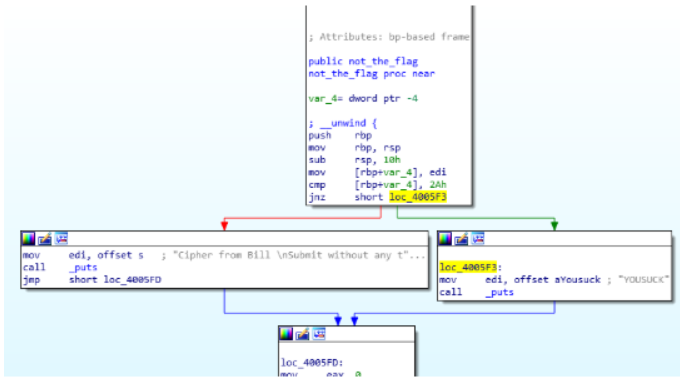
tab 反汇编
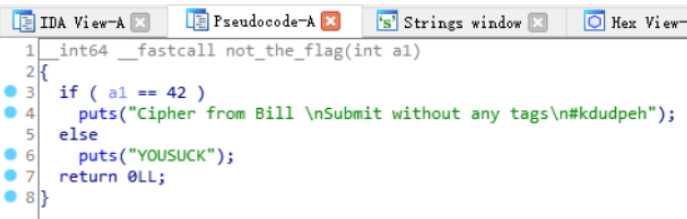
即明白了 我们在linux中应该输入42
然后他输出 Cipher from Bill \nSubmit without any tags\n#kdudpeh 猜测 kdudpeh 是我们想要的flag ISCC{kdudpeh} 提交错误 看题目注意到 sha1 以为是 sha1碰撞 后来发现是 shi1加密 获得flag为: flag{80ee2a3fe31da904c596d993f7f1de4827c1450a}