祥云杯复现
Crypto
Exposure
题目考点:
dp高位泄露 |
题目:
Do you know how to rsa? |
from Crypto.Util.number import * |
解题
参考文章:https://github.com/pcw109550/write-up/tree/master/2019/KAPO/Lenstra-Lenstra-Lovasz
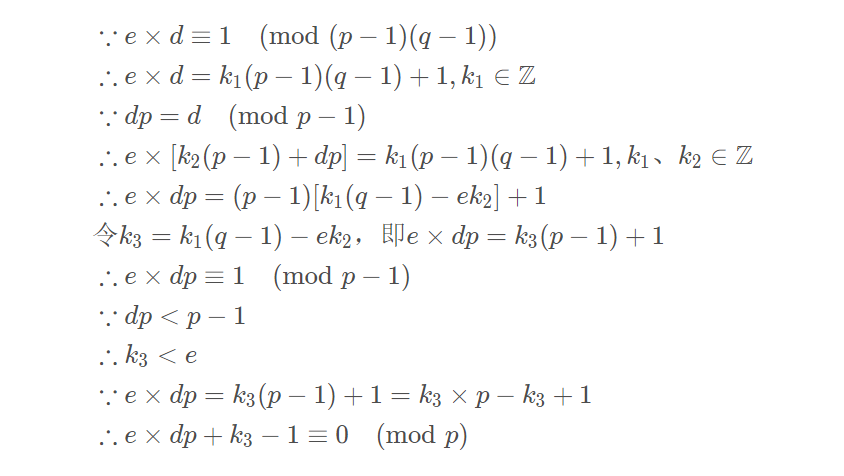
这道题知道secret = dp>>200,即已知dp的高位恢复出dp。
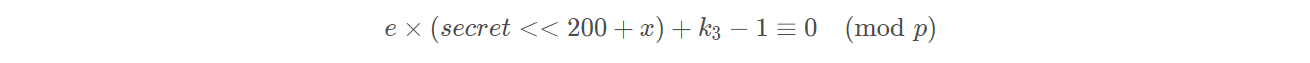
#sage |
整合脚本,获取flag。
#sage |
more_calc
题目:
maybe u need more cpu |
import gmpy2 |
解题:
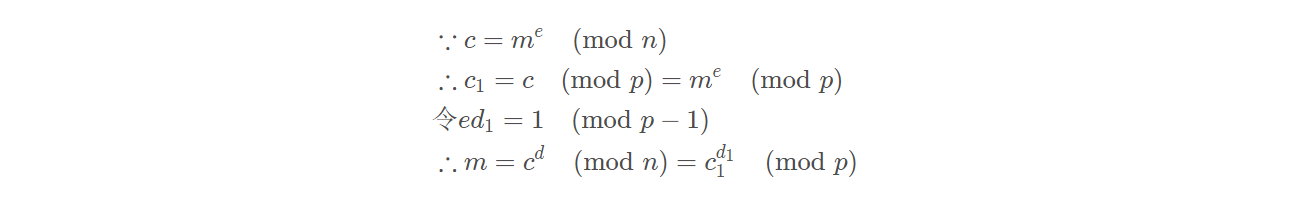
import gmpy2 |
RSAssss
题目考点:
费马因式分解 |
题目:
more factors,more strong |
from Crypto.Util.number import * |
解题:
参考文章:https://github.com/pcw109550/write-up/tree/master/2019/ISITDTU/Easy_RSA_2

exp:
from Cryptodome.Util.number import * |
simpleRSA
题目考点:
低解密指数攻击 |
题目:
Familiar and simple rsa |
from Crypto.Util.number import * |
解题:
参考lazzzaro师傅的文章。

exp:
from Cryptodome.Util.number import long_to_bytes |
RE
RE1
通过逆向发现 flag 的每一位都采用相同的加密方式,然后会在函数末尾判断,所以直接写一
个 gdb 脚本爆破明文对应密文的关系即可
gdb 脚本:
b *(0x8000000 + 0x18096) |