上海赛复现
RE
RE1 真正的Babyre
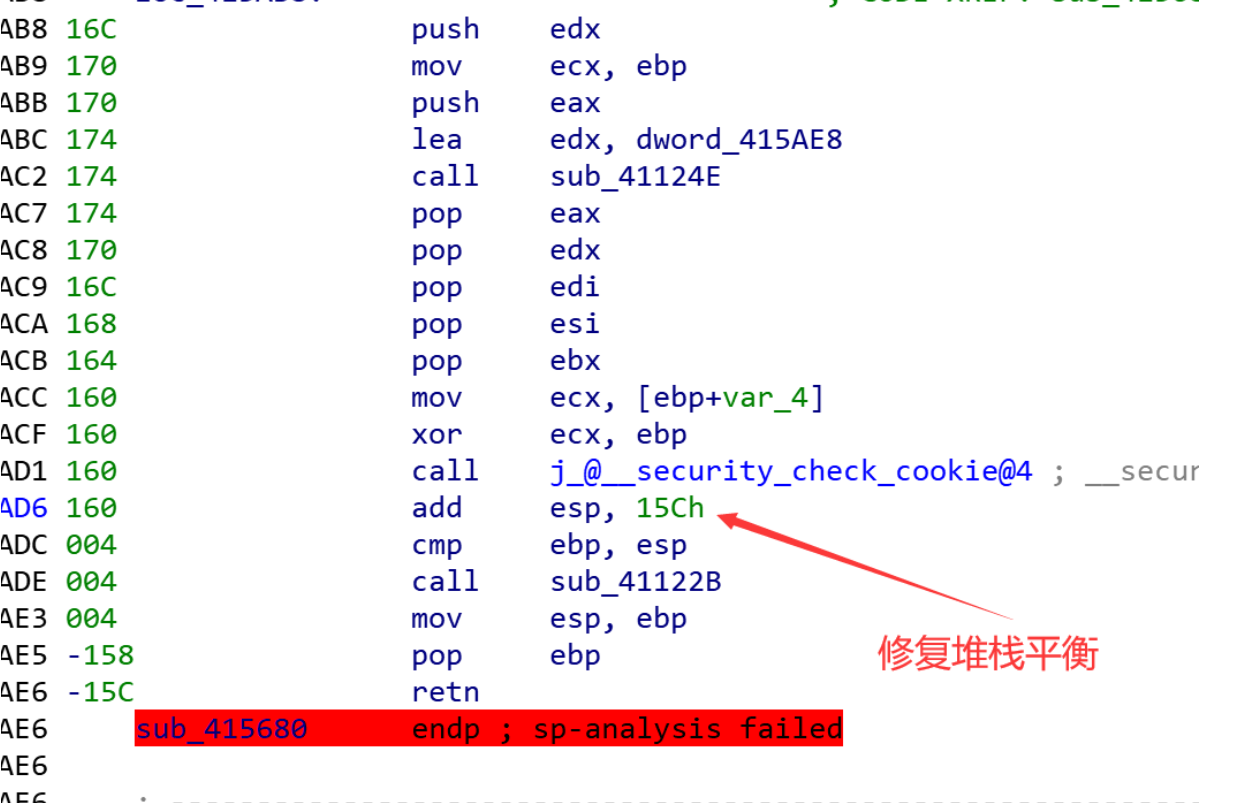
首先定位字符串,函数堆栈不平衡,首先修复堆栈不平衡问题。F5,寻找主逻辑。IDA启动调试,处理掉case3处的反调试。
dump出关键对比数据:
cipher=[0x1F, 0x18, 0x0F, 0xFA, 0xB8, 0x63, 0x64, 0x89, 0x18, 0x68, |
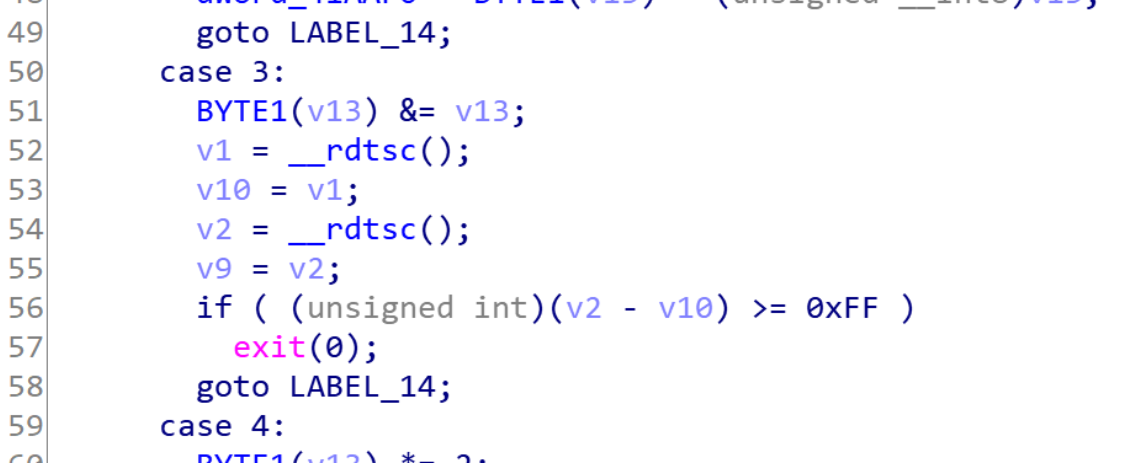
动调得出主要逻辑:flag进行两轮加密,每次取table中的对应位异或和相与,若相与后,结果不为零则将table处值*2继续异或相与。最后将异或的值与后一位flag相异或。
分析逻辑,三位flag是有关联的,猜测flag格式为“flag{}”,动调下断点,发现前几位与对比数据已经相同,并且不受后方未确定字符影响。所以选择爆破flag。python模拟程序加密,按位进行爆破。
python脚本:
cipher=[0x1F, 0x18, 0x0F, 0xFA, 0xB8, 0x63, 0x64, 0x89, 0x18, 0x68, |
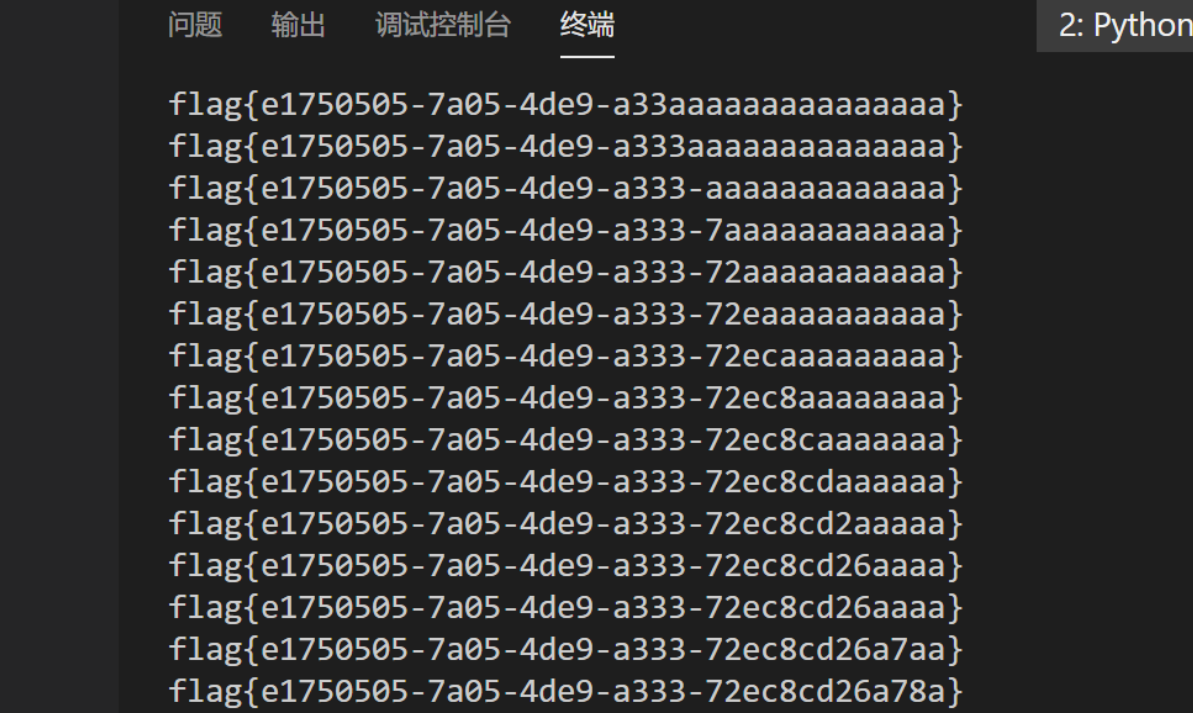
得到flag:
crypto
baby_rsa
思路:根据hint1和hint2求得p从而解题
过程:
hint1 = pow(233*p1+q1,123,n1) |
使hint1与hint2有相同的指数,由于q1前面数字为1,所以可以通过t2-t1来消除掉q1,从而提取出因子p1。
import gmpy2 |
baby_dsa
from Crypto.Util.number import * |
MISC
签到
{echo,ZmxhZ3t3MzFjMG1lNX0=}|{base64,-d}|{tr,5,6}bash 执行
pcap
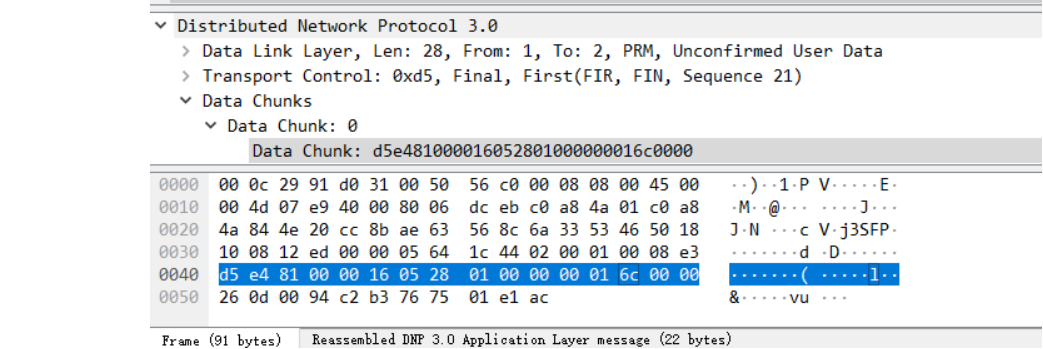
frame.len == 91
慢慢找
pcap analysis
先查modbus,发现有个长度为65,其他都62,与上题基本一样。
接着直接查frame.len == 65,拼接得到flag
flag{323f986d429a689d3b96ad12dc5cbc701db0af55}