XCTF-RE
前言
博客已经搭了有几周了,但是由于最近考试真的让我压力很大(对于菜鸡的我来说复习真的不是一件容易的事)
不想复习的我,来水水博客放松一下吧!
不说了直接暴力上题!
0x01.open-source
首先当然是下载附件啦!
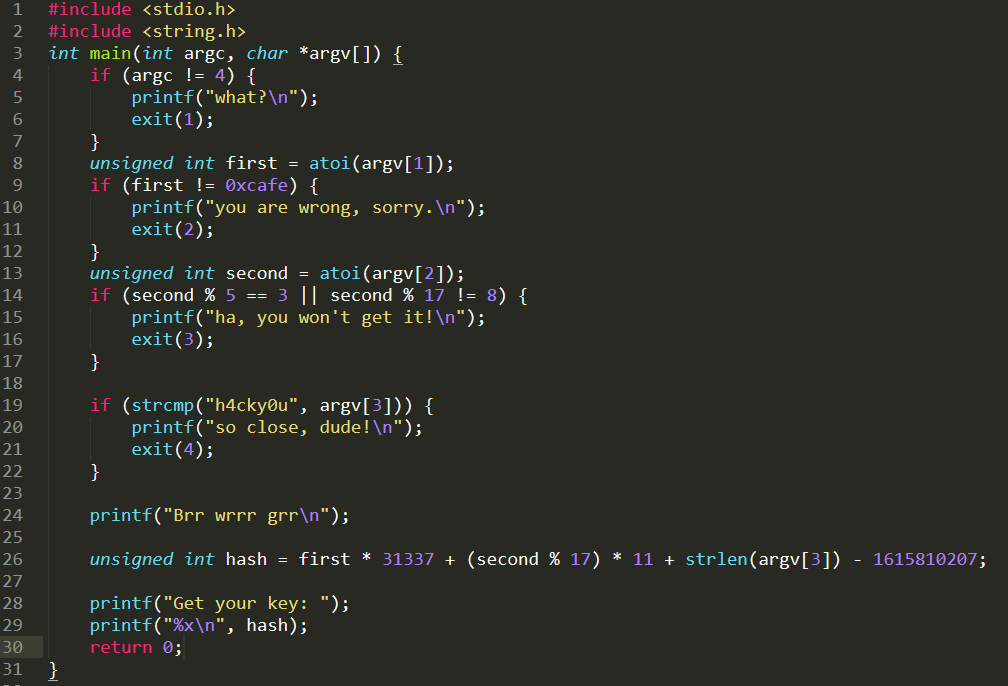
一看是一个.c文件,啥也别说直接用sublime打开
第一次上传WP到自己的网站有点小小的激动!
自我感觉这题好像跟逆向没有啥关系,让我们简单来分析一下吧!
大概浏览一遍,发现hash貌似就是我们想要的flag,所以我们需要找到first,second和 strlen(argv[3]) 三个参数
unsigned int hash = first * 31337 + (second % 17) * 11 + strlen(argv[3]) - 1615810207;
直接来看第8行,其中atoi函数,是把字符串转为数字,如atoi(“123”)就是数字123, 所以 0xcafe 即:51966
unsigned int first = atoi(argv[1]); |
再来看第13行,参数对5取余不能等于3,且对17取余等于8,发现自然数25就可以
unsigned int second = atoi(argv[2]); |
最后一个参数即argv[3]=h4cky0u!
if (strcmp("h4cky0u", argv[3])) { |
直接把三个参数的值改到程序上去
first = 0xcafe , (second%17)= 8 ,strlen(argv[3]) = strlen("h4cky0u")
现在我们编写简单脚本
#include <stdio.h> |
得到flag!!!

0x02.simple-unpack
题目描述:菜鸡拿到了一个被加壳的二进制文件
由于菜鸡本人对kali虚拟机并不是很会用,所以只能先拖入winhex里碰碰运气看看是什么壳!
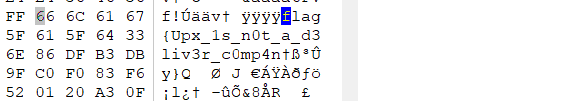
尝试在winhex查找中输入flag
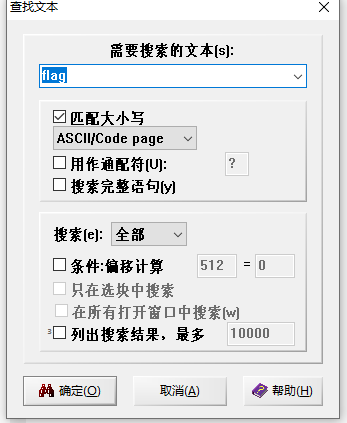
运气真好,把括号里的乱码删掉即为 flag{Upx_1s_n0t_a_d3liv3r_c0mp4ny}
0x03.logmein
这道题终于涉及到了逆向ida静态分析,让我们把它拖入ida64(提前在exeinfope查看其为64位文件),并佛系按下F5
void __fastcall __noreturn main(__int64 a1, char **a2, char **a3) |
仔细分析一下代码,发现这个for循环是找出flag的关键,写一个c++文件试一试吧
#include <iostream> |
输出就得到flag啦! flag{RC3-2016-XORISGUD}
0x04.insanity
巨巨弱觉得前面的题目太难了,来个简单的缓一下
拖入ida中直接暴力F5,好像也没啥关键信息啊,这时候就要用到ida的各种快捷键了。
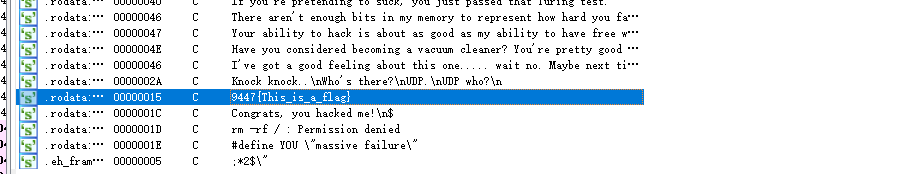
shift+F12看一看strings window中有没有什么有效信息
直接发现flag 9447{This_is_a_flag}
0x05.python-trade
下载附件发现是pyc文件,利用python反编译工具 在线工具
得到代码如下:
import base64 |
反编译的意思大概就是反着来呗!
如上代码运用for循环进行异或和加法操作最终得到base64字符串
那我们就将base64字符串在for循环里进行减法和异或操作不就得到flag了嘛?
简单脚本如下:
import base64 |
嘻嘻嘻得到flag nctf{d3c0mpil1n9_PyC}
0x06.game
直接拖入ida中,恶心人的是我没有在这道题中发现main函数,导致我无法运用万能快捷键F5
这让我如何是好,不管了shift+F12试一试
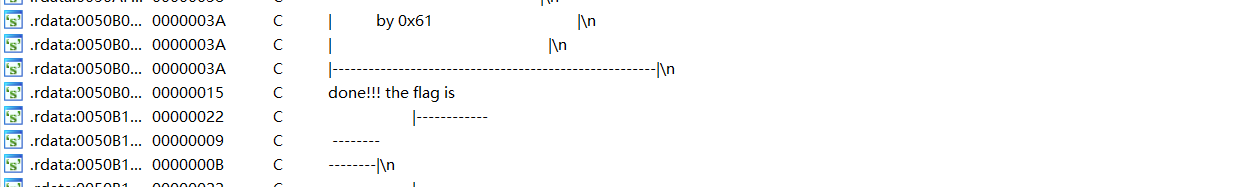
哇!我真幸运
发现了done!!! the flag is我就感觉这里一定有flag
鼠标点击flag 然后跳转到这一行
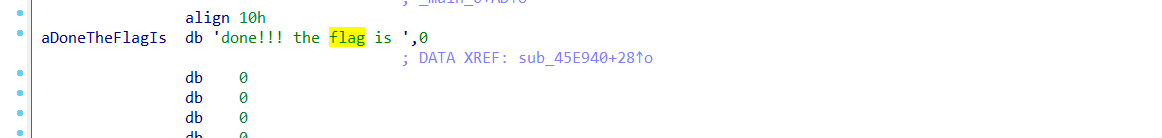
鼠标右键点击 List cross references to 并按下F5 (这一步说实话菜鸡也不太懂,于是参考了别人的博客)
终于找到了原代码!!!
sub_45A7BE("done!!! the flag is "); |
上边代码是求flag的过程,大概意思是它将程序分为了两个数组,一组为v2到v58另一组为v59~v115
将第一个数组与第二个数组异或再将值赋予第一个数组,然后第一个数组再和0x13异或,最后把第一个数组转化为字符串即为flag
思路既然懂了,那我们直接上代码:
a=[18,64,98,5,2,4,6,3,6,48,49,65,32,12,48,65,31,78,62,32,49,32,1,57,96,3,21,9,4,62,3,5,4,1,2,3,44,65,78,32,16,97,54,16,44,52,32,64,89,45,32,65,15,34,18,16,0] |
得到flag zsctf{T9is_tOpic_1s_v5ry_int7resting_b6t_others_are_n0t}